The Growing Attack Surface: How Organizations Are Struggling to Keep Pace with Cyber Threats
Digital transformation initiatives, such as cloud migration, remote work adoption, and IoT integration, have significantly expanded organizations’ attack surfaces. As IT complexity increases, many organizations struggle to scale security operations with their digital footprint beyond their firewall, creating blind spots that expose them to digital risks. The growing volume of digital assets results in more attack vectors, potential vulnerabilities, and, in turn, more significant digital and regulatory risks. This flood of information can overwhelm organizations, leading to limited visibility, information overload, false positives, and difficulty prioritizing vulnerabilities (Figure 1). Despite record-breaking investments in security tools and systems, many organizations face diminishing returns. IT complexity, data silos, limited visibility to threats occurring from outside their firewall, and lack of crucial context are undermining the effectiveness of these solutions. Alarmingly, more than 85% of enterprises have experienced data breaches, as a Frost & Sullivan survey highlighted.
Figure 1
The Rising Threat of Fraud: How Data Breaches Fuel Identity Theft and Financial Crimes
As the digital attack surface grows, cyber threats become more frequent and sophisticated. Shawn Loveland, COO at Resecurity, points out that technological advancements, such as AI, and new business models, such as ransomware-as-a-service, have intensified this threat landscape.
The shift to a cybersecurity-as-a-service model has made attacks more profitable and accessible to non-technical users, widening the pool of potential threat actors. Hackers exploit vulnerabilities in external digital assets, such as shadow IT, cloud misconfigurations, AI and LLM services, and supply chain weaknesses, as seen in the 2024 Santander attack and other high-profile data breaches. The impact is severe, including financial losses, reputational damage, and legal consequences (Figure 2). Organizations must adopt proactive, intelligence-driven strategies to combat these risks to enhance visibility, prioritize threats, and integrate security across operations. This ensures resilience against rising threats and the continued limited effectiveness of existing security products and processes. Defenders’ overreliance on AI further impacts this.
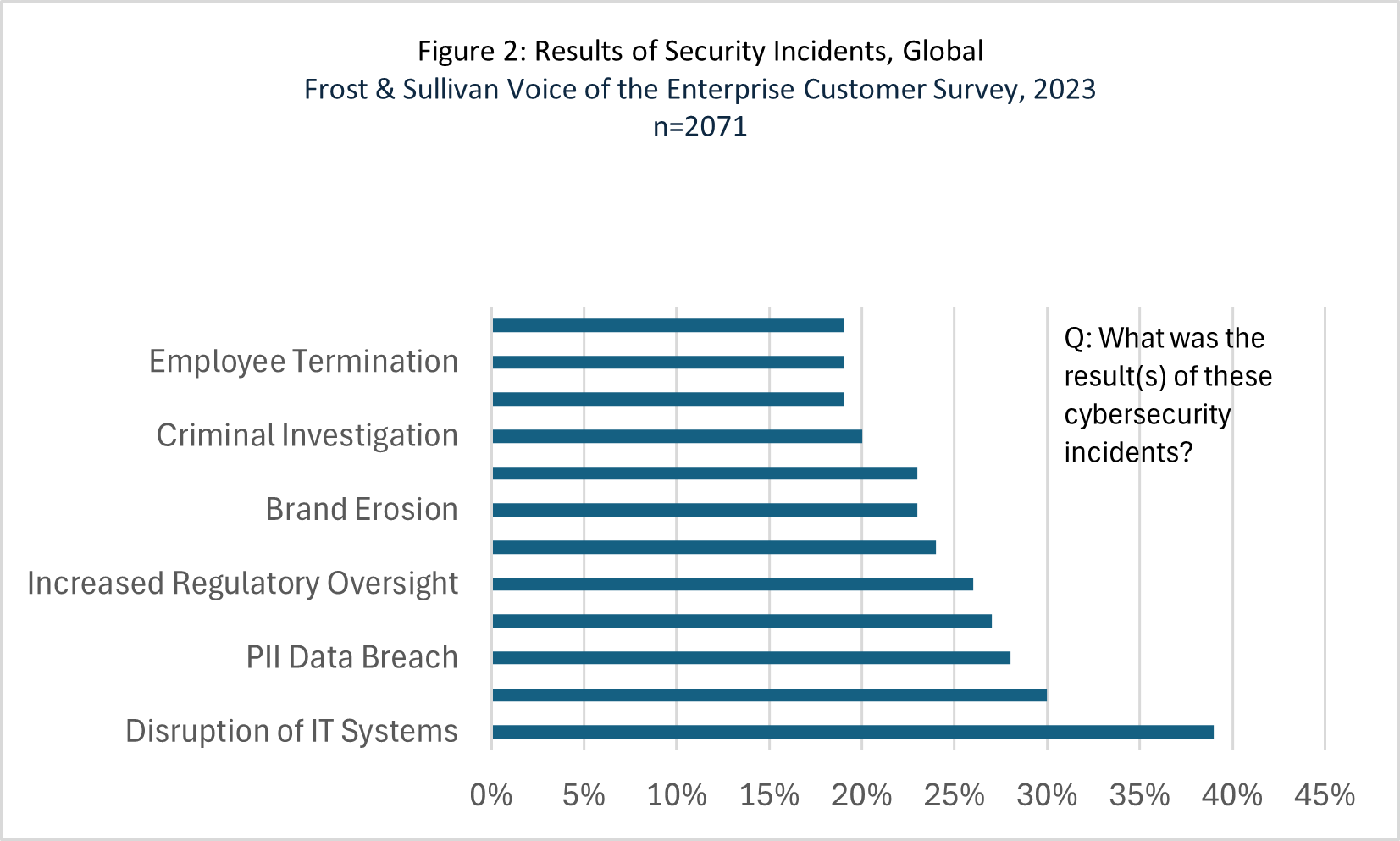
Figure 2
Discovering Hidden Threats: The Power of Actionable Insights in Complex Cyber Environments
Organizations must develop visibility and context into the evolving threat landscape to address the challenges posed by an expanding attack surface and increasingly sophisticated threats. Threat intelligence (TI) delivers actionable insights into the threats targeting an organization, enabling a deep understanding of the dynamic and evolving threat environment.
A TI ecosystem consists of several key components that address distinct cybersecurity needs, which are progressively converging to provide comprehensive data breach and fraud detection and prevention:
- Cyber threat intelligence (CTI) provides actionable insights into emerging threats, focusing on tactics, techniques, and procedures (TTPs) that can lead to breaches or fraud. Thus, it enables proactive defense.
- Threat intelligence platforms (TIPs) centralize and analyze threat data, offering a comprehensive view of potential data breaches and fraud risks across channels.
- Digital risk protection (DRP) identifies and mitigates external threats, such as dark web activity, exposed credentials, and brand impersonation, all linked to data leaks and fraud.
- External attack surface management (EASM) discovers and secures digital assets, offering visibility into the attack surface and third-party risks, reducing the potential for breaches and fraud.
By integrating these solutions into a single platform, organizations gain a unique perspective on vulnerabilities, supply chain risks, and emerging threats, enabling proactive defense strategies. This unified approach enhances efficiency, decision-making, and effectiveness, helping organizations detect leaked data, prevent phishing and fraud attacks, address vulnerabilities, and stay ahead of evolving threats.
Transforming Security with Impactful Threat Intelligence

In addition to direct fraud prevention, dark web intelligence lowers incident response costs and mitigates reputational damage. Banks that monitor discussions and leaks on hidden forums can respond more promptly to breaches, thereby decreasing “dwell time”—the period from an attacker’s initial infiltration to the total containment of the threat. Research, including studies by IBM and the Ponemon Institute, consistently reveals that quickly identifying and addressing threats can result in millions of dollars in savings related to breach incidents. Overall savings can be significant when considering legal fees, customer notification requirements, recovery efforts, and reputation damage—especially for organizations managing large amounts of sensitive data. Therefore, while the aggregate financial benefits may differ between banks, dark web intelligence offers substantial protection against financial losses and operational disruptions in today’s complex cyber threat landscape.
Conclusion
In an era of expanding attack surfaces, profitable criminal strategies, and sophisticated threats, such as AI-enabled attacks, threat intelligence is essential for identifying data leaks, fraud, and emerging risks. TI integrated into security operations offers actionable insights, improves visibility, and minimizes the attack surface. As the threat landscape changes, proactive and innovative strategies are essential to reduce risks and bolster overall security. To discover how TI can benefit organizations, view an exclusive webinar hosted by Resecurity and Frost & Sullivan.





